Rebranding at KYOS

A new identity for even more expertise With the aim of constantly listening to our employees and our stakeholders in a more global sense, we at KYOS concluded that it was time to take advantage of the redesign of our website to update our visual identity. This was an opportunity to implement a major rebranding […]
Thales HSM vs DpoD Cloud

High Assurance Hardware Security Modules Secure your sensitive data and critical applications by storing, protecting and managing your cryptographic keys in Luna Network Hardware Security Modules (HSMs) – high-assurance, tamper-resistant, network-attached appliances offering market-leading performance.
Exchange zero-day Exploit

Whether you are a Kyos customer or not, considering the criticality of this flaw, we offer you a free primary investigation of your Exchange server, to determine if it is still vulnerable, as well as to identify if any potential attacks have taken place, which we know is very likely. Even though Kyos Exchange Servers have not been affected, 50% of our customers with on-premise Exchange Servers have been impacted, despite the application of the patch that we performed the same day.
0-day Vulnerability

On March 2, Microsoft has released an emergency security update for Microsoft Exchange to remediate six vulnerabilities allowing remote code execution, of which 4 can bypass any authentication control.
What is Double Key Encryption (DKE)?

1. Introduction What is DKE? DKE – or Double Key Encryption– is a new option offered by Microsoft Information Protection (MIP), a cloud-based data classification and protection software. Given that many customers are worried to start their journey to the cloud because of data protection concerns, Microsoft implemented a new option to protect unstructured data […]
Security of data in the cloud

The concept of Cloud has evolved in the last 20 years, and security concerns have grown with it. The first serious effort to provide data hosting in the Cloud comes with Amazon Simple Storage Service (S3), and with it the security burden to make sure that correct permissions were configured to avoid private data to become public.
Kyos Security Essentials
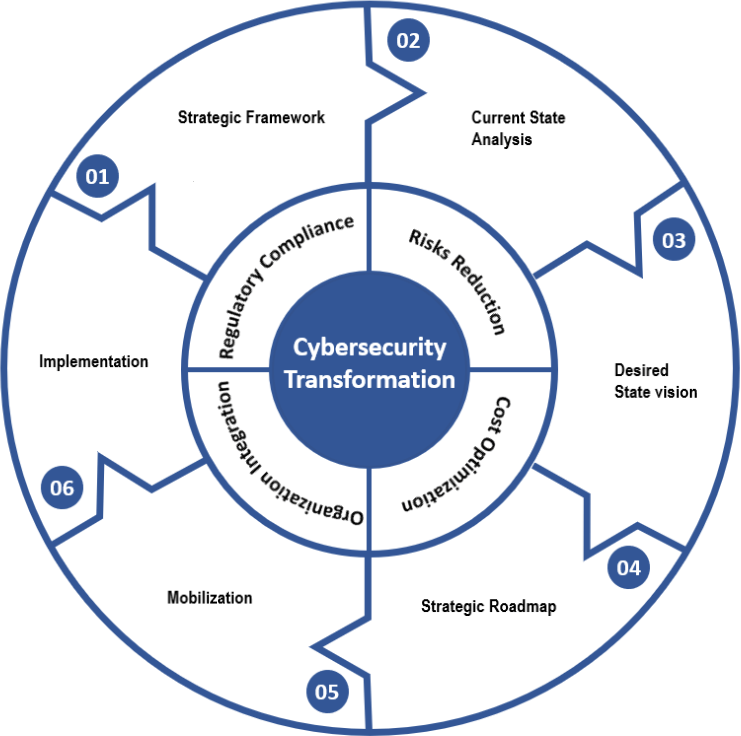
Grâce à l’expérience accumulée lors de nombreux Kyos Security Essentials chez nos clients nous avons décidé d’adapter cette offre packagée afin de mieux répondre aux besoins des clients et à l’évolution des risques en cybersécurité et des controles CIS (Center for Internet Security).